Attaching lambda, secret manager execution role with AWS-CDK
If you are not familiar with the stack creation check out AWS-CDK basics and Lambda.
In this post we are directly deep diving into IAM roles and attaching IAM roles to lambda.
Here we are taking example of lambda execution roles and secret manager read write.
Check here how to fetch secret manager details using AWS-SDK.
To our existing cloudformation stack we are going to add the following code.
const role = new iam.Role(stack, `lambda-execution-role`, {
assumedBy: new iam.ServicePrincipal('lambda.amazonaws.com'),
description: 'An example IAM role in AWS CDK',
managedPolicies: [
iam.ManagedPolicy.fromAwsManagedPolicyName('service-role/AWSLambdaBasicExecutionRole'),
iam.ManagedPolicy.fromAwsManagedPolicyName('service-role/AWSLambdaVPCAccessExecutionRole'),
iam.ManagedPolicy.fromAwsManagedPolicyName('SecretsManagerReadWrite'),
],
});
const hello = new lambdaNode.NodejsFunction(stack, `lambda-hello`, {
entry: path.join(__dirname, 'hello/src/hello.ts'),
timeout: Duration.seconds(30),
vpc,
role,
securityGroups: [securitygroup],
handler: 'handler',
environment: {
FUNCTION_NAME: 'hello',
},
});
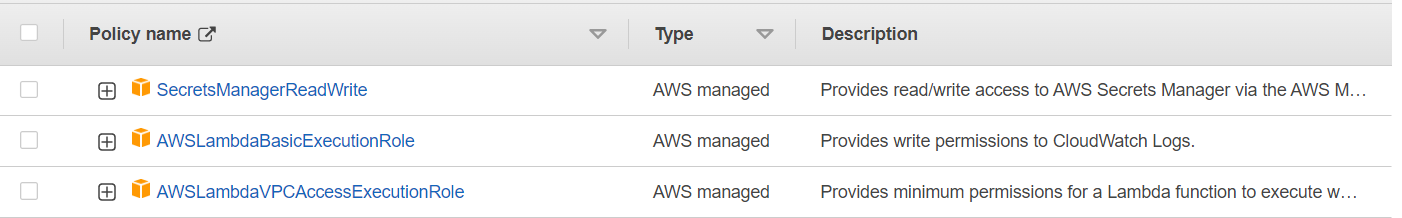
Our policy role would look something like this.
We have successfully attached the policies required for lambda.👍






Thank you so much for this content.
ReplyDelete